Security Assessment
What would you like us to Develop or Implement today for your Cloud or On-Prem Infrastructure?
Portfolio 😃 Details
Security Assessment
Security Assessment
Portfolio 😃 Details

Proactive Vulnerability Discovery: Securing Your Cloud Infrastructure
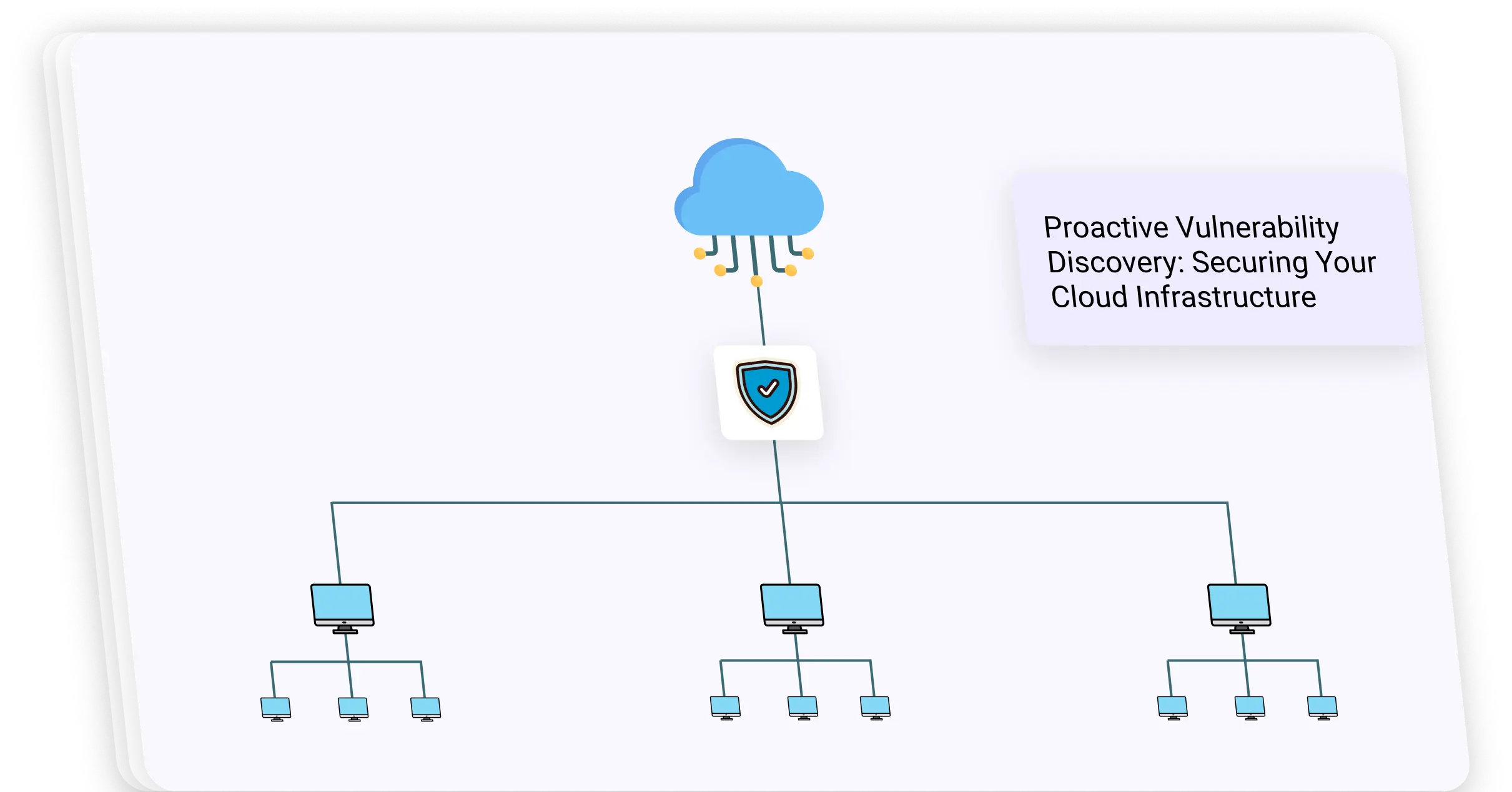
At CLOUDIDEA, we employ a comprehensive process that enables organizations to discover weak points in their cloud infrastructure before adversaries do. Our security assessment identifies vulnerabilities, configuration weaknesses, and potential threats, analyzing both the configurations of cloud service provider accounts and potential risks from the internet and within the cloud itself.
Portfolio 😃 Details

Security Assessment Checklist
Security Assessment Checklist
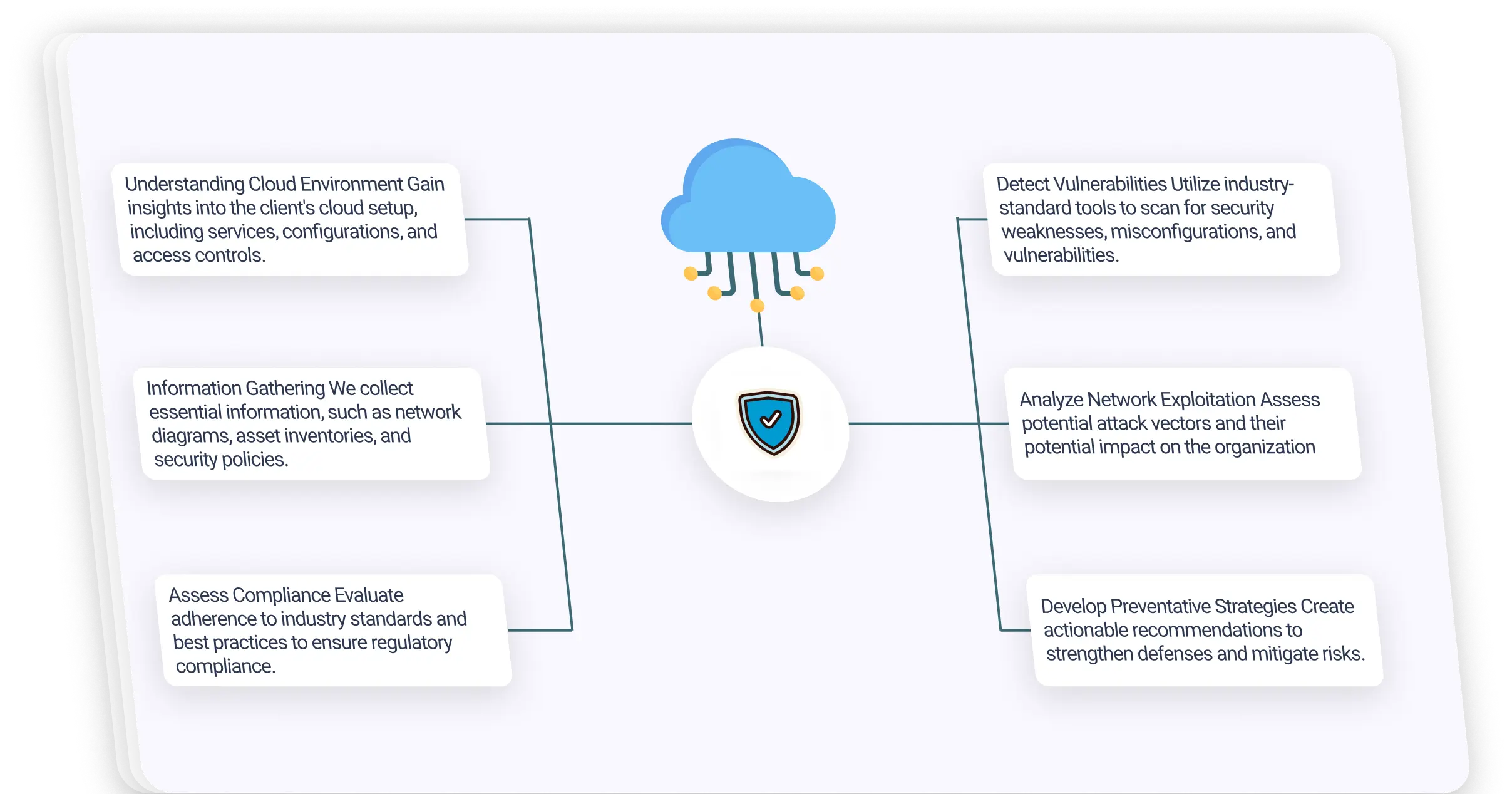
A cloud security assessment involves thoroughly analyzing an organization’s cloud infrastructure to identify and mitigate security issues.
Understanding Cloud Environment Gain insights into the client’s cloud setup, including services, configurations, and access controls.
Information Gathering We collect essential information, such as network diagrams, asset inventories, and security policies.
Assess Compliance Evaluate adherence to industry standards and best practices to ensure regulatory compliance.
Detect Vulnerabilities Utilize industry-standard tools to scan for security weaknesses, misconfigurations, and vulnerabilities.
Analyze Network Exploitation Assess potential attack vectors and their potential impact on the organization
Develop Preventative Strategies Create actionable recommendations to strengthen defenses and mitigate risks.
Our Promise
We ensure that business operations can continue without interruption in the event of a security incident, providing peace of mind to our clients.Empower Your Cloud with Seamless Help Desk Support Your Cloud, Your Support—Anytime, Anywhere. Experience our state-of-the-art help desk services with full confidence
Portfolio 😃 Details

Common Cloud Security Risks

- Unmanaged Attack Surface Exposure of unnecessary services or endpoints can create vulnerabilities.
- Human Error Mistakes made by personnel can lead to security incidents
- Misconfiguration Incorrect settings can leave cloud resources exposed to threats.
- Data Breach Unauthorized access to sensitive data can have severe consequences.
Strategy and Planning
Network security is a critical aspect of protecting data and maintaining the integrity of information systems. It encompasses various practices and technologies designed to safeguard networks from unauthorized access, misuse, malfunction, modification, destruction, or improper disclosure
Ready to Work, Lets Chat
Our team of experts is ready to collaborate with you every step of
the way, from initial consultation to implementation

