Security Operation center
What would you like us to Develop or Implement today for your Cloud or On-Prem Infrastructure?
Portfolio 😃 Details
Security Operation center
Security Operation center
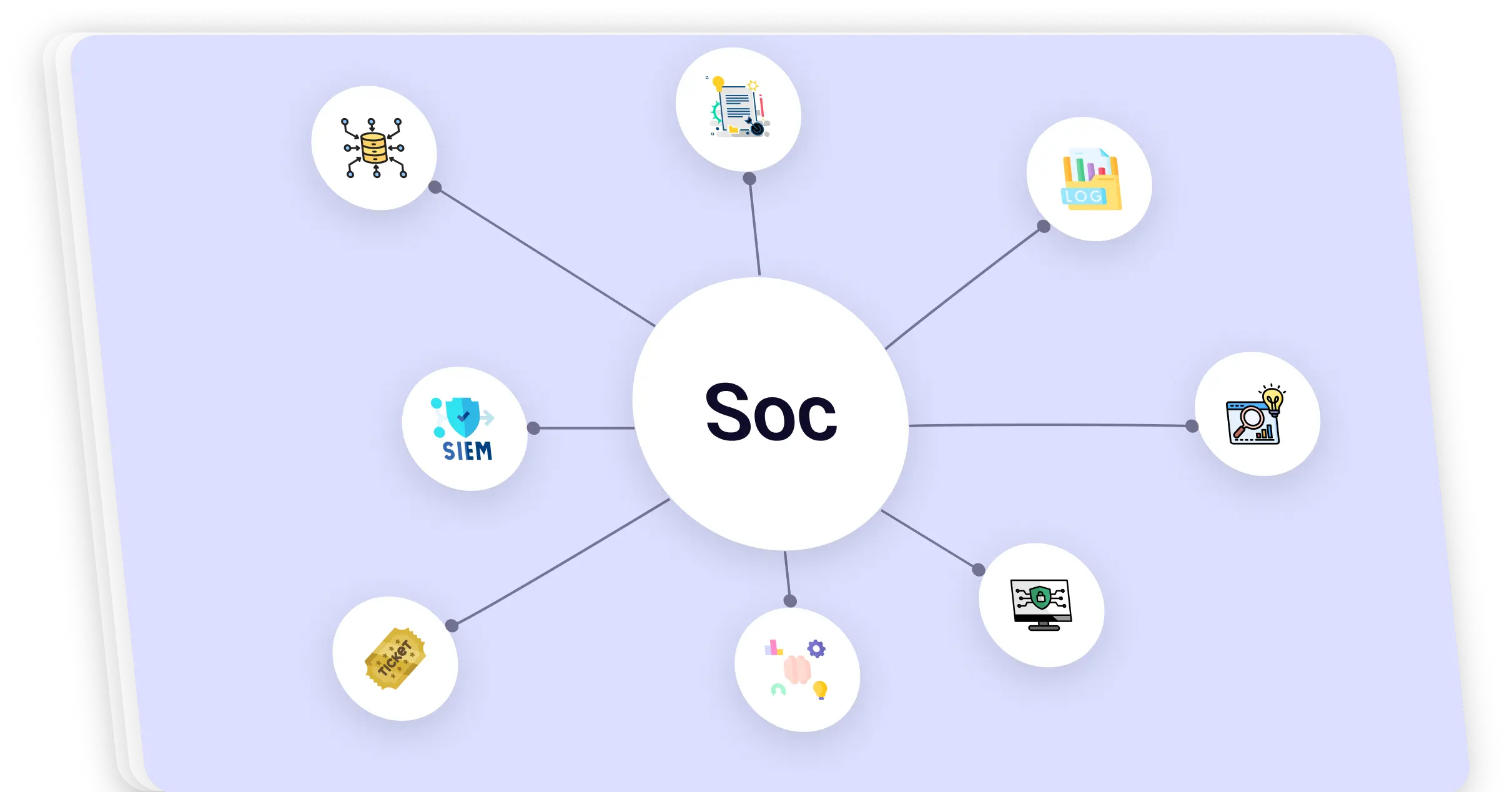
Portfolio 😃 Details

Your Business is in SAFH HANDS
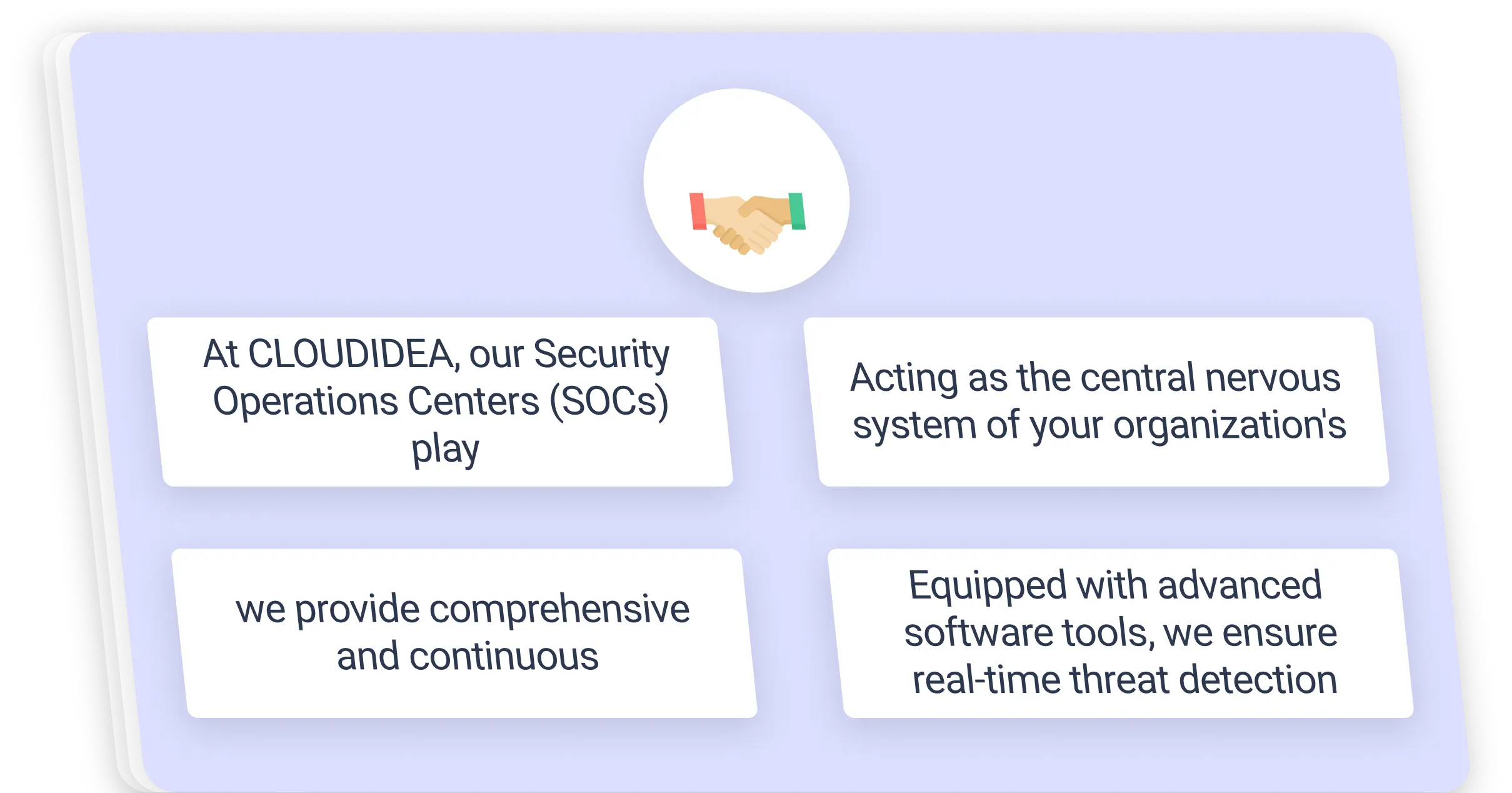
CLOUDIDEA Experience Speaks
At CLOUDIDEA, our Security Operations Centers (SOCs) play a critical role in safeguarding your digital assets and infrastructure. Acting as the central nervous system of your organization’s cybersecurity framework, we provide comprehensive and continuous monitoring and analysis of your security posture.
Equipped with advanced software tools, we ensure real-time threat detection and swift incident response.
Portfolio 😃 Details

Benefits You Can Get

- Enhanced Threat Detection and Response With sophisticated tools and skilled professionals, CLOUDIDEA enables organizations to swiftly detect and respond to threats, identifying potential issues before they escalate into serious breaches.
- 24/7 Monitoring Cyber threats don’t adhere to a 9-to-5 schedule. Our SOCs operate around the clock, ensuring constant vigilance over your network for any suspicious activity.
- Cost-Effective Security By centralizing security operations, our SOCs reduce the overall cost of cybersecurity, streamlining the incident response process and eliminating the need for multiple security solutions.
- Continuous Vigilance We offer a multitude of benefits that enhance your cybersecurity measures, providing the expertise and technology required to defend against the ever-evolving landscape of cyber threats
How We Deal with Cybersecurity Threats
Our approach to incident response is a critical component of our SOCs’ operations.

- Preparation We establish a comprehensive incident response plan, Including policies, communication strategies, and tools necessary for effective responses.
- Identification Our teams continuously monitor network traffic, logs, and alerts to detect potential security incidents. Once a potential threat is identified, we confirm whether it is a false positive or a genuine incident.
- Containment After confirming an incident, our immediate priority is to contain it. This may involve isolating affected systems to prevent the threat from spreading.
- Eradication Once contained, our SOC teams work to eliminate the root cause of the incident, which may involve removing malware, closing security gaps, and updating defenses.
- Recovery We focus on restoring and validating affected systems to ensure they are no longer compromised and can return to normal operations
- Lessons Learned After resolving an incident, our SOC team reviews the event to understand what happened, why it happened, and how to prevent similar incidents in the future. This often leads to improvements in our processes and security posture
• Advanced Tools and Technologies
Throughout this incident response process, our SOCs utilize a variety of advanced tools and technologies to assist in each phase, including automated alerting, threat intelligence, and forensic analysis-crucial for a swift and effective response.
• Use of Artificial Intelligence (AI)
We are increasingly incorporating artificial intelligence (AI) into our incident response processes. Al helps automate threat identification, provides predictive analytics to prevent future incidents, and assists in analyzing large volumes of data to identify patterns indicative of security breaches.
• Incident Response
The incident response process showcases the strategic importance of our SOCs within your organization’s cybersecurity framework. By following a structured approach, CLOUDIDEA minimizes the impact of security incidents, helping to maintain the trust of stakeholders and customers alike
Ready to Work, Lets Chat
Our team of experts is ready to collaborate with you every step of
the way, from initial consultation to implementation

